I recently posted the process of configuring iSCSI on ESXi with the Pure Storage FlashArray. One of the things I left out is (optional) CHAP security configuration. It is a pretty straight forward process but worth writing down to save anyone who wants to configure it a few document cross-reference checks.
So first what is CHAP? It has nothing to do with CHUD (Cannibalistic Humanoid Underground Dwellers), but instead an added level of security on top of the iSCSI storage protocol called Challenge-Handshake Authentication Protocol. It is not technically just for iSCSI of course, but that’s the focus here. The full name of CHAP actually really describes exactly what CHAP does–imagine that.
The CHAP process involves authenticating a host iSCSI initiator with a target iSCSI port–both sides can play both roles or just one–this depends on if the authentication is one-way or bi-directional. More on that in a bit.
As I understand it, the process is as so: a requester establishes a network link/connnection to an authenticator. The authenticator, in response, then sends a challenge to the authenticator in the form of a message. The requester then forms a response that is a hash of the challenge and the secret. The secret (essentially a password) is known to both the requester and the authenticator prior to this exchange–it is provided by an administrator. The authenticator, which knows both the challenge and the secret, looks at the hash and compares it to what it thinks the hash should be based on this information. If it is identical, the session is authenticated because this shows the requester indeed knows the correct secret. This method allows for authentication without having to ever directly send the password between the two ends. This handshake is then attempted again and again at random intervals to maintain the connection.
So I mentioned that both the host initiator and the array target port can play both the role of a requester and the role of an authenticator. What does this mean?
iSCSI CHAP allows for two authentication directions:
- The array authenticates the host.
- The host authenticates the array.
Just one mode can be chosen, or both or of course none of them.
VMware offers five CHAP modes during configuration:
- None–CHAP is not attempted.
- Use unidirectional CHAP if required by target–Tries no CHAP, then reverts to CHAP if the target requires it.
- Use unidirectional CHAP unless prohibited by target–Tries CHAP and then reverts to nothing if CHAP isn’t required/not-configured on the target.
- Use unidirectional CHAP–Tries CHAP and fails if not required/not-configured on the target.
- Use bidirectional CHAP–Tries CHAP both ways and fails if not required/not-configured/not attempted on the target.
If you plan on using CHAP I’d recommend just using either 4 or 5. This way you don’t get false positives like you could get with 3. I am going to configure bidirectional here for completeness. Unidirectional configuration can be easily inferred from it though.
VMware offers a few locations you can configure CHAP–on the Software iSCSI adapter or on the specific target. I recommend doing this on a target basis–this allows for more granular control and support for non-CHAP and CHAP environments on the same adapter. Furthermore, you can set this up on the FlashArray first or from inside VMware first–it doesn’t really matter. I am going to start with VMware.
NOTE: I am using a Software iSCSI Initiator–some limits apply to independent hardware iSCSI initiators such as you cannot configure CHAP per target and some of the CHAP security levels (like bi-directional) are not supported. Check out vSphere documentation if an independent hardware iSCSI initiator is in your configuration.
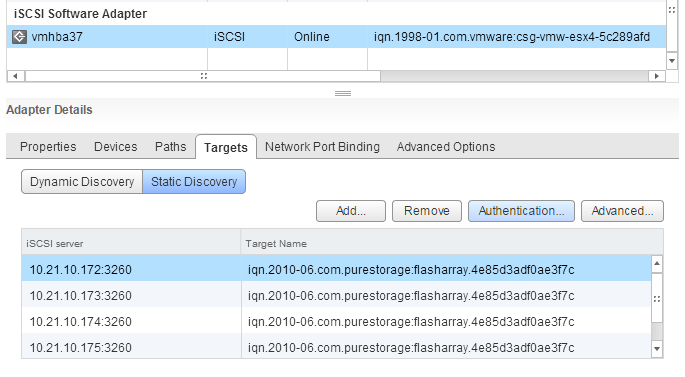
Login to the vSphere Web Client and locate your Software iSCSI Initiator in the “Manage” screen of a host under “Storage” > “Storage Adapters”. Click on the “Targets” tab and then the Static Discovery button. Select the correct iSCSI target of the target FlashArray in the list and then click the “Authentication…” button up and to the right.
It is important to note that currently CHAP configured with dynamic discovery is not supported by the FlashArray. Dynamic discovery in general is, but CHAP credentials in conjunction will not work–regardless whether you try to enter them on the dynamic target and let them inherit down to the auto-populated static targets, or enter them to the static targets populated automatically, it will not work. CHAP must only be used with static targets that have been entered manually, one-by-one.
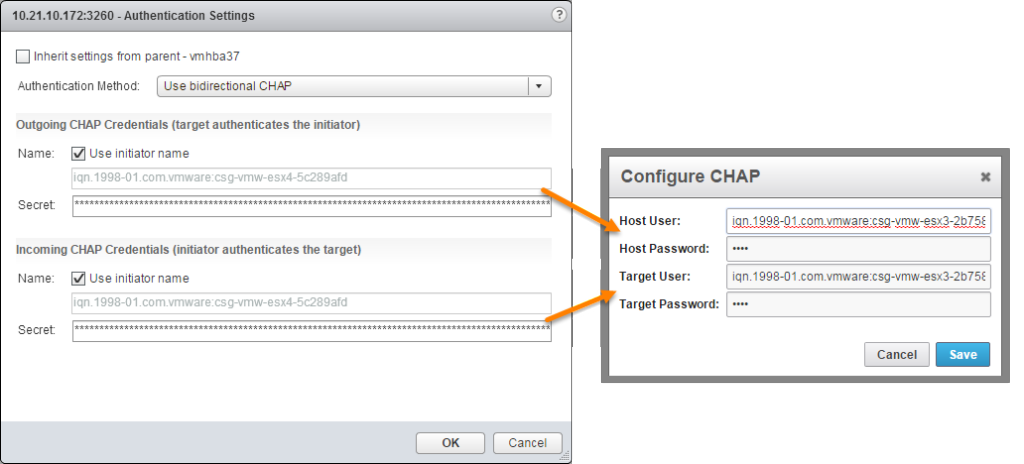
Moving forward, deselect “Inherit settings from parent” so that we can make specific CHAP information for the target FlashArray sessions. For the CHAP security level, I am going to select bidirectional. This means both the array will authenticate the host and the host will authenticate the array–a two-way handshake.
The next step is to choose a name and secret for the CHAP authentication for both incoming and outgoing handshaking. I don’t know of a lower limit for length of the name in VMware but there is a hard upper limit of 511 characters. That being said, the FlashArray has a limit of 255 characters, so keep the name below that (shouldn’t be too hard). As for the secret, I do not know of a lower limit in VMware but there is a 12 character lower limit for the secret on the FlashArray and once again an upper limit of 255 characters. So keep the password between 12 and 255. VMware documentation also indicates that only alphanumeric characters are supported (and I know that older versions of ESX had some issues with using special characters). So avoid using special characters unless you hear differently from VMware.
Lastly, the secrets for the host and target cannot be the same. So make them different. Make the name something that makes sense to you. VMware allows you to just use the IQN by clicking a box so I am going to do that.
Enter in the information and click OK.
The secret is masked and there isn’t any password verification-like box so I’d recommend typing it in a word professor and then copy and pasting it into the field to make sure to avoid typos.
Now login to the FlashArray GUI to configure the target side of things. The CHAP information must be added by clicking on the “Storage” tab and then on the specific host–this cannot be done at the host group level. Once the proper host is select click on the “Details” sub-tab and then the gear icon to the right and select “Configure CHAP”.
Enter in the same information that you added into the ESXi host. Enter in the names you chose and the respective passwords and click “Save”.
Note that the information entered in both sides correlate exactly, top to bottom, like shown in the below figure.
You can now provision volumes to the host! Repeat the process on each host as necessary.







So you recommend to add chap at the target level. So if I’ve got 4 targets on a single host I need to make that change 4 times. I’m assuming that the secrets need to be the same on each target since there is only one place to enter that info on the host on the Pure.
Yeah all of the targets are going to have the same secrets for that particular host. I haven’t tried configuring the secret at a higher level (like the vmhba) but in cases of multiple FlashArrays that would require you to have the same target secret on all of them (unless you overrode them individually) so I think it might be best to just do it at the static target level, since it is a one-off thing.